work hardening program example
The effective capability set represents all capabilities the process is using at the moment this is the actual set of capabilities that the kernel uses for permission checks. A brute force password-cracking program was used to see how long it would take to guess each password.

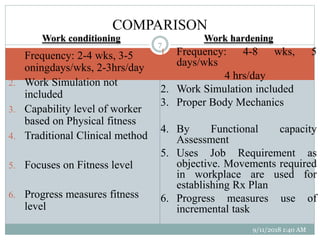
Work Conditioning And Work Hardening
A human passenger is not required to take control of the vehicle at any time nor is a human passenger required to be present in the vehicle at all.
. The two initiatives need to work in concert with each other for both to be successful. Bloomberg Law has an interesting article by Bobby Magill about efforts to. For example some workloads vertically autoscale themselves.
Call encryption uses Transport Layer Security TLS and Secure Real-time Transport Protocol SRTP. There are settings you may want to adjust to control comments users and the visibility of your user information. Use the below command example to restart a systemd service in order to apply new updates.
By Mike McMillan for the USFS. For example most firewalls can be configured to restrict the number of simultaneous connections from any individual IP address or network thus preventing a range of simple attacks. The term implies that the atrophied part was of a size normal for the individual considering age and circumstance prior to the diminution.
At onset there are usually no symptoms but if they develop symptoms generally begin around middle age. So the system hardening process for Linux desktop and servers is that that special. In atrophy of an organ or body part there may be a reduction in the number or in the size of the component cells or in both.
For example an attacker could have a workload on the node change itself to run as a more privileged service account that exists in the same namespace. Specifically restrictions restrictions can be applied to any public keys that are present in the sshauthorized_keys. Change of any kind is hard but getting employees to care about data governance can be especially difficult.
An extremely crucial part of hardening any system is to ensure that it is always kept up. In this final step you will implement various additional hardening measures to make access to your SSH server as secure as possible. Organizations that view Data Governance and IT Policy separately will struggle.
One program which can be used to allow scripts to run as different users is suEXEC which is included with Apache as of 12 and is called from special hooks in. They may contain sensitive or confidential data from memory. Certain cells and organs normally undergo atrophy.
Some firewalls offer additional options to give far greater flexibility. Systemctl restart httpdservice 15. For example some CMS applications are writeable by the user allowing a user to install whatever extensions they want.
The particle source provides the particles such as protons or electrons that are to be accelerated. When severe it can result in coronary artery disease. For file capabilities the effective set is in fact a single bit indicating whether the capabilities of the permitted set will be moved to the effective set upon running a binary.
The following tips and tricks are some easy ways to quickly harden an Ubuntu server. An autonomous car can go anywhere a traditional car goes and do everything that an experienced human driver does. Step 4 Advanced Hardening.
For example if a professional with less training such as a massage therapist or exercise coach could address your problem your OT should. Core dumps are intended to help determine why a program aborted. The result of aerial ignition on the Moose Fire August 2 2022 in Idaho.
OpenSSH server can impose restrictions on a per-key basis. Yet the basics are similar for most operating systems. On a Sun Ultra 5 with 512MB of RAM and a 333MHz processor the first password hello took less than five seconds to crack.
The system should be configured to prevent setuid programs from creating core dumps. The security configuration framework is designed to help simplify security configuration while still allowing enough flexibility to allow you to balance security productivity and user experience. Identify the services that are listening on specific ports using the following ss command.
State officials announced about a month after the school shooting in Uvalde an additional 1055 million to support school safety and mental health initiatives statewide through August 2023 which. Because the algorithm used by PGP normally the RSA algorithm is essentially unbreakable PGP offers a highly secure way of encrypting files at rest especially when used alongside a Threat Detection and Response SolutionIn fact this algorithm is so secure that it has even been used in high-profile malware. Atrophy decrease in size of a body part cell organ or other tissue.
Besides certifications and straightforward customer communication you want call encryption in 2020. There are many aspects to securing a system properly. Ss -tulpn To list all installed services with their output status issue the below command.
This is the same amount of time it would take to guess most words in the English language or a word in any other. We are defining discrete prescriptive Windows 10 security configurations levels 5 through 1 to meet many of the common device scenarios we see today in the. Unencrypted networks are prone to snooping.
For many people high cholesterol levels are due to a diet that is too high in saturated fats and trans fats. Employee and executive program buy-in. For example Windows Defender Firewall allows you to specify a program instead of port number.
Atherosclerosis is a pattern of the disease arteriosclerosis in which the wall of the artery develops abnormalities called lesionsThese lesions may lead to narrowing due to the buildup of atheromatous plaque. The field of occupational therapy is extremely diverse and OT evaluations will look different in a NICU compared to a work hardening program but overall evaluations follow this general structure. Particle accelerators use electric fields to speed up and increase the energy of a beam of particles which are steered and focused by magnetic fields.
The goal is to enhance the security level of the system. How does a particle accelerator work. Who is the Florida PACE Funding Agency.
High blood cholesterol levels can cause hardening of the arteries at a younger age. An autonomous car is a vehicle capable of sensing its environment and operating without human involvement. The file permissions are another example of a default setting that can be hardened.
While convenient this can allow an attacker who has already compromised a node to escalate further in the cluster. System hardening is the process of doing the right things. Add the following line to the etcsysctlconf file.
It is recommended that core dumps be disabled or restricted. These VoIP protocols work together to establish high-grade security in every call. Other factors that can contribute to hardening of the arteries include.
As always we want to minimize access to Postgres so it would be quite normal to create a rule for TCP andor IPv6 traffic arriving on port 5432 to be rejected or black-holed. FPFA is an interlocal agreement created and established as a separate legal entity public body and unit of government pursuant to Section 163017g Florida Statutes with all of the privileges benefits powers and terms provided for therein and by law. A third use of PGP is to encrypt files.
Core principles of system. Family history of hardening of the arteries. Operating system hardening should be implemented before any services are hosted whether the system be in a production or development environment.
Difference Between Work Hardening And Work Conditioning Difference Between

Muscular System Essay Example Essay Examples Essay Muscular System

Pdf Cognitive Work Hardening A Return To Work Intervention For People With Depression

Facts About Taekwondo Infographic Wing Chun Martial Arts Taekwondo Training Martial Arts

Pdf Cognitive Work Hardening A Return To Work Intervention For People With Depression

What Is A Work Hardening Program Simmons And Fletcher P C
Pdf Cognitive Work Hardening A Return To Work Intervention For People With Depression

Pdf Work Hardening Occupational Therapy In Industrial Rehabilitation

Work Conditioning And Work Hardening

Work Conditioning And Work Hardening

What Is Pascal S Law Or Principle Definition Formula Examples Equation Derivation Pascal S Law Common Law Force And Pressure

Work Conditioning And Work Hardening

Work Conditioning And Work Hardening

Department Expense Budget Template Departmental Budget Template The Departmental Budget Template And Its Budget Template Budgeting Meeting Agenda Template

Scrum We Don T Deliver A Working Increment Every Sprint Scrum Scrum Master Agile